Example SOCKS Configuration (Telesploit Server)
Host: IP address or Fully Qualified Domain Name of target
Port: Application port
Example SOCKS Configuration (Telesploit Client)
Host: localhost (127.0.0.1)
Username: <NONE>
Password: <NONE>
Port: Assigned SOCKS port
The Telesploit server can act as a SOCKS proxy for SOCKS aware applications. For example, this service can be used to connect a database application on the Telesploit client to a database within the target environment. Unlike the other services, the SOCKS proxy does require additional configuration on the Telesploit server and is limited to a single target at a time.
From a Telesploit server console navigate to the /root/telesploit directory and run the script socks_up.sh. This allows the SOCKS proxy configuration to be modified and starts the service.
./socks_up.sh
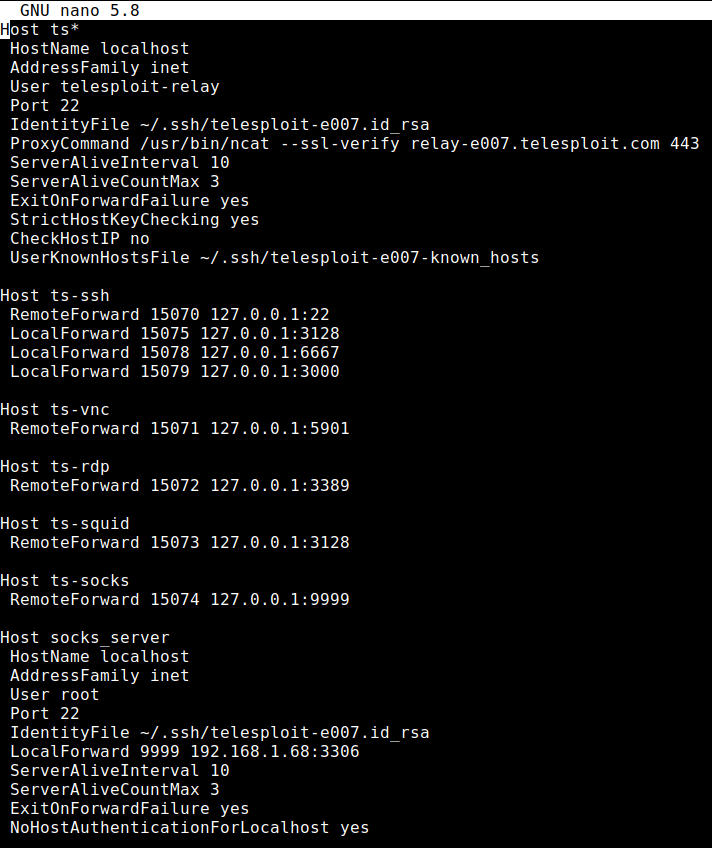
The /root/.ssh/config file is opened for editing.
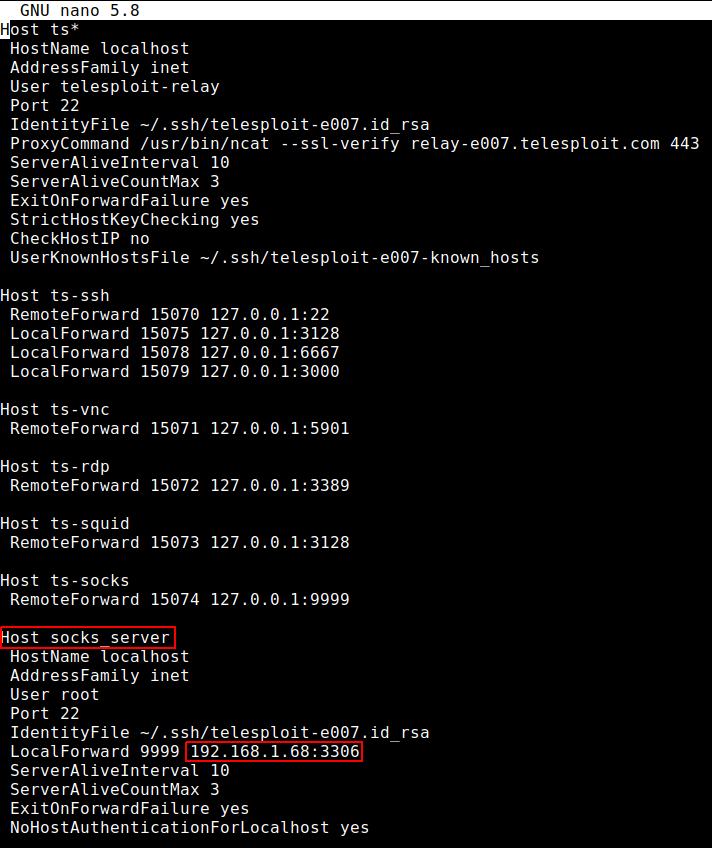
Under the “Host socks_server” section modify the IP address and port number to match the target. In the following example the SOCKS proxy traffic is forwarded to a MySQL database (port 3306) running on an internal machine that is accessible from the Telesploit server, but not directly from the Telesploit client.
On the Telesploit client configure the application with the assigned SOCKS port. In this example a SQuirreL SQL client is used to access the MySQL database.
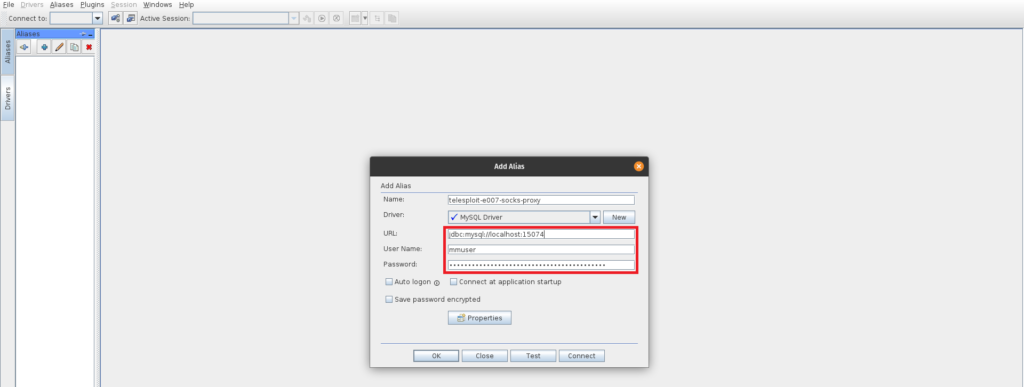
The target can then be accessed as if the application were being run from the Telesploit server itself.
Once testing is complete, the socks_down.sh script can be run to close the SOCKS proxy connection.
./socks_down.sh